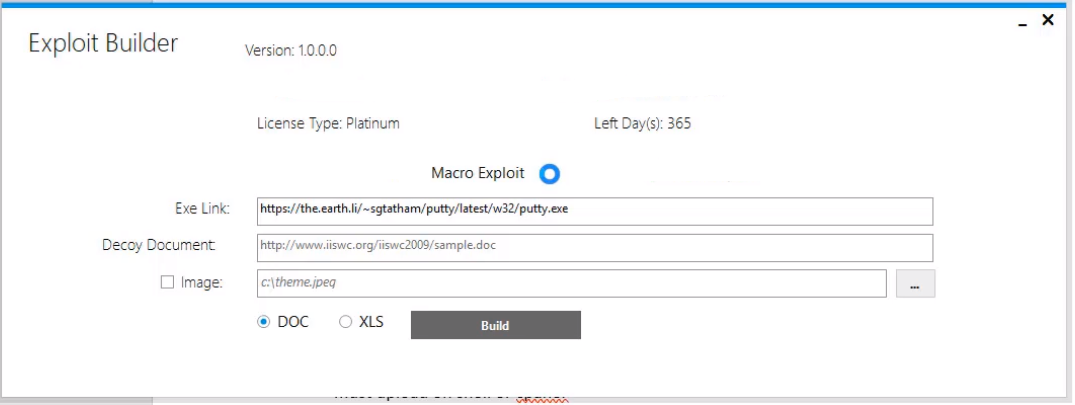
Exploit Builder
Using our doc exploit is very simple, and doesn’t require you to be a cybersecurity expert.
This vulnerability allows remote code execution every time a user opens a specially modified Microsoft Office Word (doc exploit) with an invalid Word file Stream.
Our Office DOC Exploit Builder 2020 is the most powerful solution you can find for any penetration testing scenario. You can follow the simple step by step process in order to build your doc exploit, and you can rest assured that the resulting file will be 100% undetectable, from all commercial and known anti-virus and anti-malware programs.
How to use doc exploit builder?
STEP 1 – CHOOSE EXE FILE
All you have to do in order to convert your .exe into a doc file, is to register the doc first and then choose the .exe to host on any kind of hosting area file and follow next simple steps.
STEP 2 – Grab file link
Once the crypted .exe file is uploaded on any host , then you have to fetch that file’s URL link. Place that link in Builder to create the doc file.
STEP 3 – All set
once the link will be place in builder your doc file will be processed . Its ready to spread .
Stay updated with our YouTube Channel for Latest Updates.You may also like.
whats app : +15853263397